Recent high profile data breaches & impacts on the cyber liability market
In recent months we have observed an unprecedented rate of high profile cyber breaches impacting millions of everyday Australians and shining a spotlight on apparent deficiencies in cyber and privacy protection within organisations across the country. The frequency and severity of the incidents have left many organisations wondering how they can keep the data they hold protected amidst ever-more sophisticated hacks by cyber criminals.
In the case of the September 2022 Optus breach, the Federal Government responded with the harshest condemnation and rhetoric heard to date, saying companies should be doing vastly more to prevent data breaches occurring. Prime Minister Anthony Albanese stated:
“When customers hand over their data to companies in Australia they expect that it will be kept safe and this kind of data breach should be an absolute wake up call to corporate Australia.”
The government has refused to foot the bill for replacement Medicare cards and passports for the millions of customers affected in the Optus breach, insisting the telco compensate its customers directly. The cost of identity document replacement alone, for affected customers, is expected to run into the 100s of millions of dollars.
Optus has received much criticism for the breach but commentary from cyber experts points to a wide-spread issue within Australia rather than an isolated lapse by a single company.
At the heart of this issue is the fact that historically there has been a more relaxed approach to the safekeeping of personal data in Australia. Our privacy laws and related penalties are less stringent compared with USA, UK and EU. For example, there is currently a $2.2M limit on corporate penalties in Australia. By comparison the EU’s General Data Protection Regulations hold companies liable for up to 4% of annual revenue. For Optus, whose revenue in FY21 was $7B, that would mean a penalty of up to $280M.
Added to this, there has been a lack of regulatory funding in Australia perhaps due to the fact that data protection has not been a high profile issue – but this is rapidly changing. As more individuals continue to be impacted, companies face much more scrutiny of their data protection practices and that increased scrutiny has revealed some alarming facts.
In October 2022 Medibank was the victim of another cyber attack which appears to have resulted, at least in part, from a lack of Multi-Factor Authentication (MFA) protocols. MFA is widely recommended as part of any prudent cyber security programme. Bellrock has frequently observed that the availability of Cyber Insurance relies upon a range of data protection mechanisms being in place – invariably this includes MFA. MFA is regarded as the best protection against ransomware attacks. Thus begging the question – how could Australia’s largest private health care insurer not have adequate privacy protection procedures in place especially where it holds health information?
The impact of these two high-profile Australian companies being compromised in quick succession has been significant. We are now seeing these important issues being discussed by industry leaders and politicians on both sides of politics. This may instigate the fast-tracking of privacy law reform that has been absent in recent years.
Importantly, businesses are taking notice of the potential significant costs they are exposed to (either by way of regulatory action/penalties) or civil actions (claims for compensation and related legal costs) following a cyber attack.
Overview of cyber incidents in 2022
The Office of The Australian Information Commissioner (OAIC) has released data showing that while the total incidence of notified cyber breaches in the first half of 2022 has fallen 14% compared to the previous 6 month period, the incidence of large breaches (those involving the data of 5000 or more people) has increased by 33 per cent.
The tables below give some insights into the nature of the breaches and sectors most frequently targeted.
41 per cent of all data breaches resulted from cyber security incidents. The table below shows the breakdown by category.
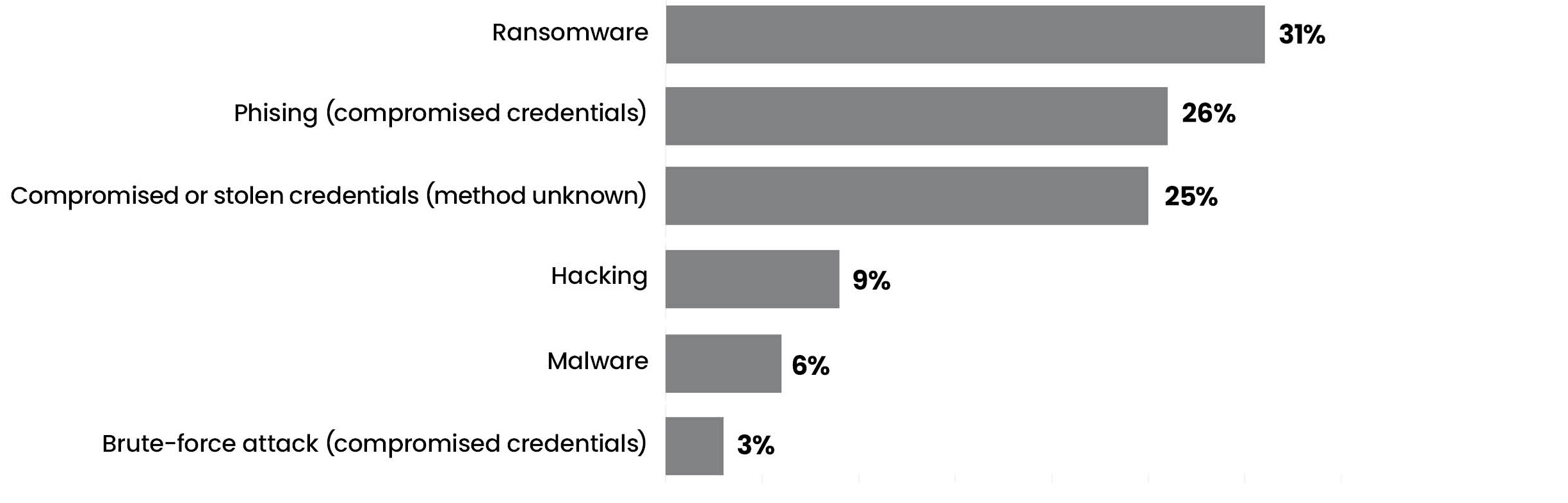
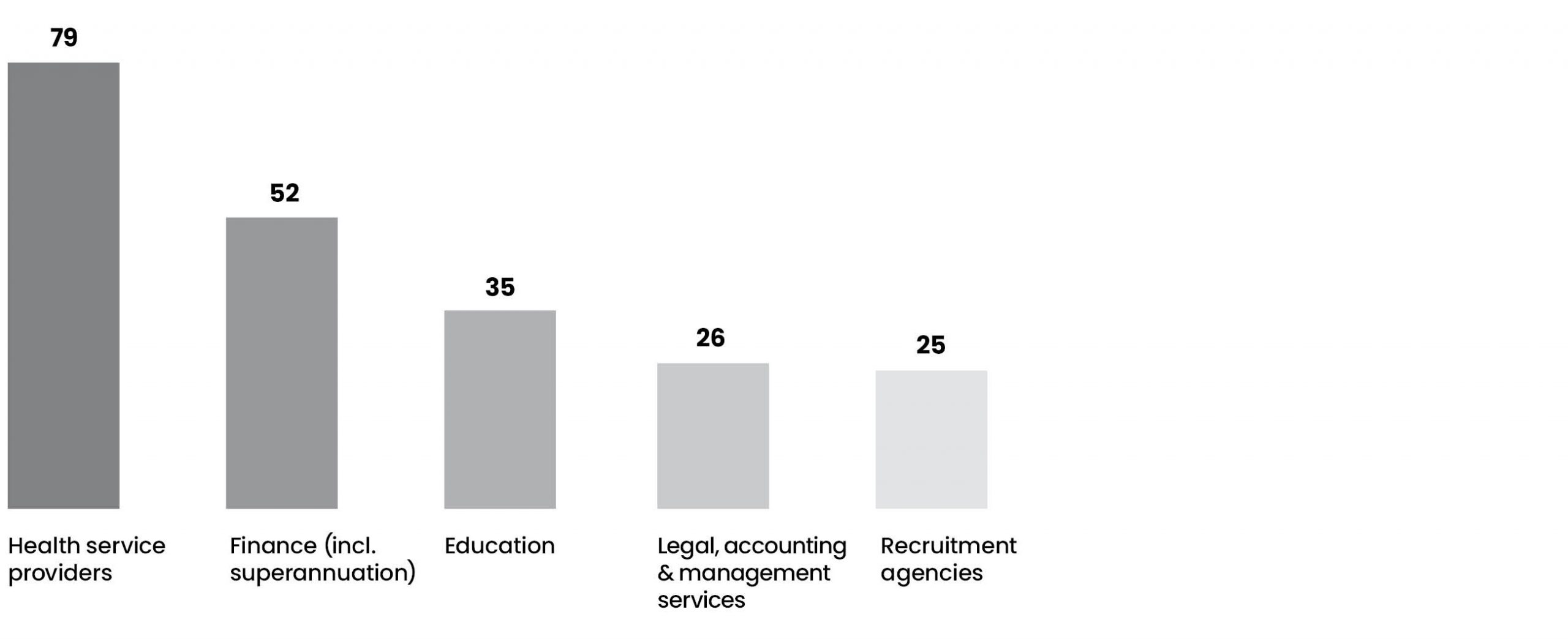
| Company | Date | Impact |
| Optus | October 2022 | Data of 9.8M customers compromised with 2.8M of those “severely impacted” |
| Woolworths MyDeal | October 2022 | Data of 2.2M customers impacted |
| Vinomofo | October 2022 | 500,000 user records sold on dark web |
| Medibank | September 2022 | 200 GB customer data stolen |
| August 2022 | 5M user accounts impacted | |
| Icare | June 2022 | 193,000 claimant’s data breached due to human error |
| Spirit Super | May 2022 | Data leak exposes 50,000 user accounts |
| Samsung | March 2022 | 200GB of confidential client data stolen and internal source code leaked |
| Toyota Motor Group | March 2022 | Factory operations suspended after hack resulting in 13,000 vehicles delayed |
| Medlab | February 2022 | Data of 223,000 customers impacted with a portion of data published on dark web |
| NSW Government | February 2022 | Data of 500,000 NSW residents leaked |
| Red Cross Australia | January 2022 | Data of 515,000 vulnerable people stolen |
Government & industry responses
- The Australian Federal Police (AFP) has launched Operation Hurricane to investigate the criminal aspects of the Optus breach.
- Operation Guardian has also been launched as a joint partnership with the AFP, the private sector and industry to combat cybercrime.
- A new “Anti-Scam Centre” has been announced with $10M in funding going to the Australian Competition and Consumer Commission for the project.
- Legislation is currently before parliament to tighten up privacy laws & increase penalties for data breaches.
- A more stringent industry code for telcos was published by Communications Alliance in October to better protect consumers from fraudulent transactions.
- Amendments to the SOCI Act which came into effect in July this year mandate a series of cyber security & reporting obligations for organisations deemed “responsible entities”. See our article on this topic here.
How can businesses limit exposure to cybercrime?
Though it is not possible to prevent targeting by cyber criminals, or to stop an attack at its source, there are many ways organisations can reduce their vulnerability to cybercrime.
- Stay informed & aware: The Australian Cyber Security Centre (ACSC) releases an annual report detailing trends and data relating to cybercrime. It is also possible to register for the ACSC alerts service for real time warnings of new threats and incidents.
- Conduct a Cyber Risk Assessment: Every organisation has a unique range of vulnerabilities dependent on size, structure, systems used and the industry you operate in. Bellrock recommends all clients undertake a Cyber Risk Assessment with our third party experts to accurately identify cyber risk.
- Develop an incident response plan: The speed and efficacy of your response to a cyber incident can limit its impact. There are also laws governing notification of incidents (see our article on the SOCI Act here). It is important to ensure you have an appropriate plan in place and that all key staff are aware of what to do in the event of a cyber incident.
- Develop a business continuity plan that involved actions following a cyber incident: Planning for how your business can move forward after an incident takes place is crucial.
- Ensure adequate Cyber Liability Insurance is in place: Your broker can assist in recommending an appropriate risk management programme which includes Cyber liability insurance.
How do the spate of recent attacks impact the cyber insurance market?
The recent spate of cyber attacks has brought cyber security, cyber preparedness and the utility of cyber insurance as a risk transfer tool to the fore.
Lloyds recently stated that cyber risks have the potential to expose insurers to systemic risks that they (and their reinsurers) may struggle to meet. The cyber insurance market continues to harden.
Insurers have taken the following steps (albeit depending on the unique characteristics of the risk):
- Updating policy wordings to provide clarity as to the cover being provided. All policies placed at Lloyds now specify whether cyber is provided or specifically excluded
- Increasing premiums
- Declining to offer terms where insureds do not meet minimum prerequisites for cyber security. Insurers are now more often requesting evidence of improvements in cyber security to ensure cover remains in place and as a ‘carrot’ to provide renewal terms for the subsequent period
- Offering free cyber security training.
It has been reported that Australian companies’ spending on cyber insurance could grow by 70 per cent over the next 24 months to $800 million.
The current threat of significant increases in fines by regulators will also give insurers reasons to increase rating for the cover. This, along with the ongoing frequency and severity of attacks will also give insurers reason to increase rate however we expect rate changes to be applied to medium to large organisations that are more data-driven and thus at heightened exposure of an attack rather than small enterprise.
For further information or advice relating to Cyber Liability Insurance, please contact us via the form below.




